← program evaluation consulting logo University of california berkeley summative assessment eyfs examples Formative vs summative assessment comparison chart →
If you are looking for Top vulnerability assessment and management best practices | Sysdig you've visit to the right page. We have 35 Pics about Top vulnerability assessment and management best practices | Sysdig like Hazard Vulnerability Analysis Template, Hazard Vulnerability Assessment (HVA) Tool | ASHE and also Hazard Vulnerability Assessments. Here it is:
Top Vulnerability Assessment And Management Best Practices | Sysdig
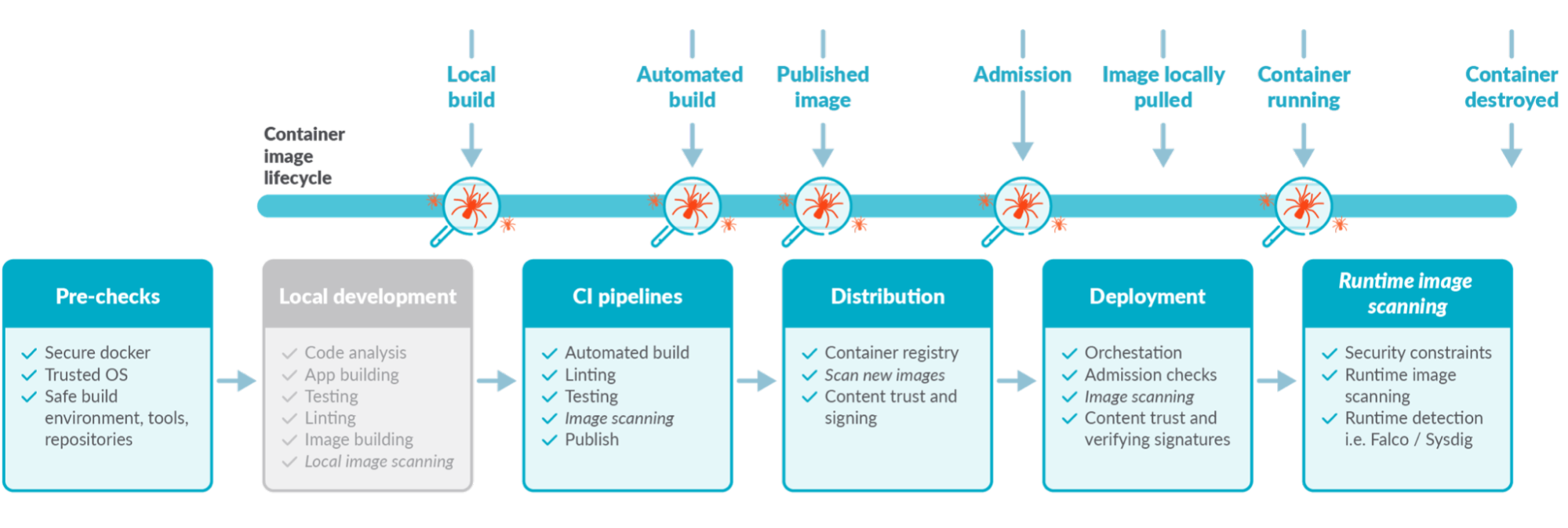 sysdig.com
sysdig.com
vulnerability practices assessment dockerfile security sysdig scanning container lifecycle vulnerabilities docker comparing deploy
Urban Climate Change Vulnerability And Risk Assessment Framework
 www.researchgate.net
www.researchgate.net
Solved Conduct A Hazard Vulnerability Analysis, Using The | Chegg.com
 www.chegg.com
www.chegg.com
Risk Assessment Recording - GAR Training Services
 www.gar-trainingservices.co.uk
www.gar-trainingservices.co.uk
risk assessment recording gar hse
Hazard Vulnerability Analysis Template For Your Needs
 lesboucans.com
lesboucans.com
hazard analysis vulnerability sampletemplates
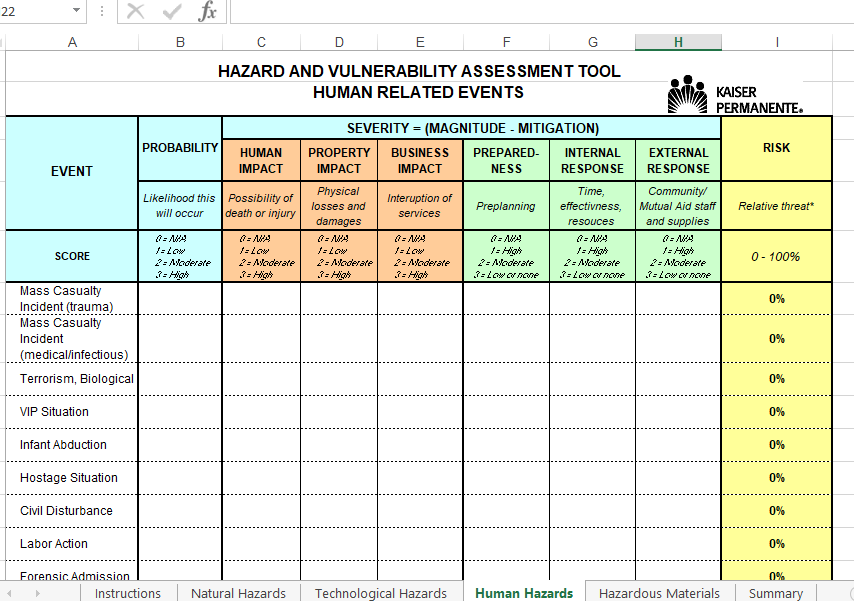
HAZARD AND VULNERABILITY ASSESSMENT TOOL NATURALLY | Chegg.com
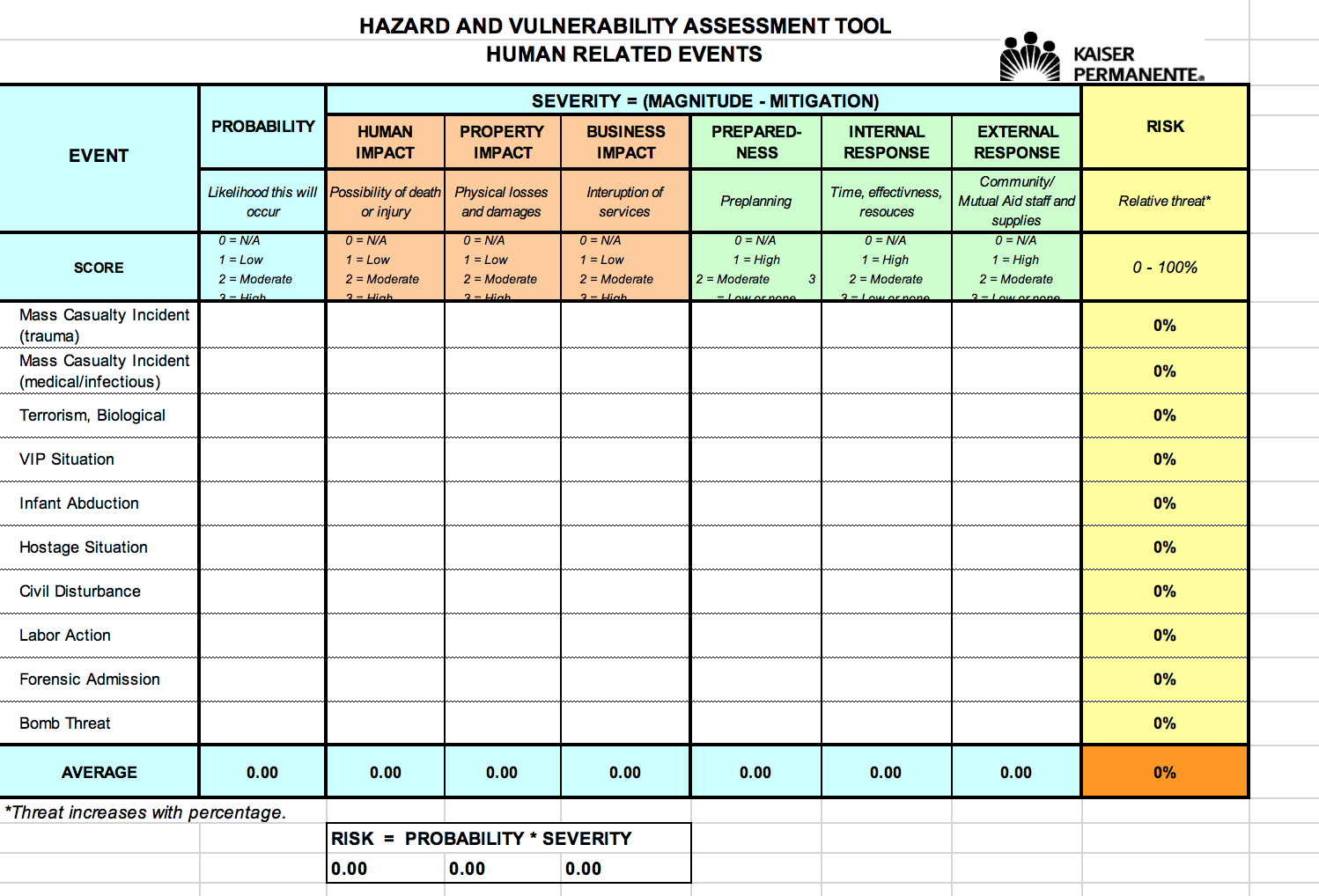 www.chegg.com
www.chegg.com
vulnerability hazard kaiser permanente conduct spreadsheet
Vulnerability And Threat Assessments For Higher Ed: What Are They And
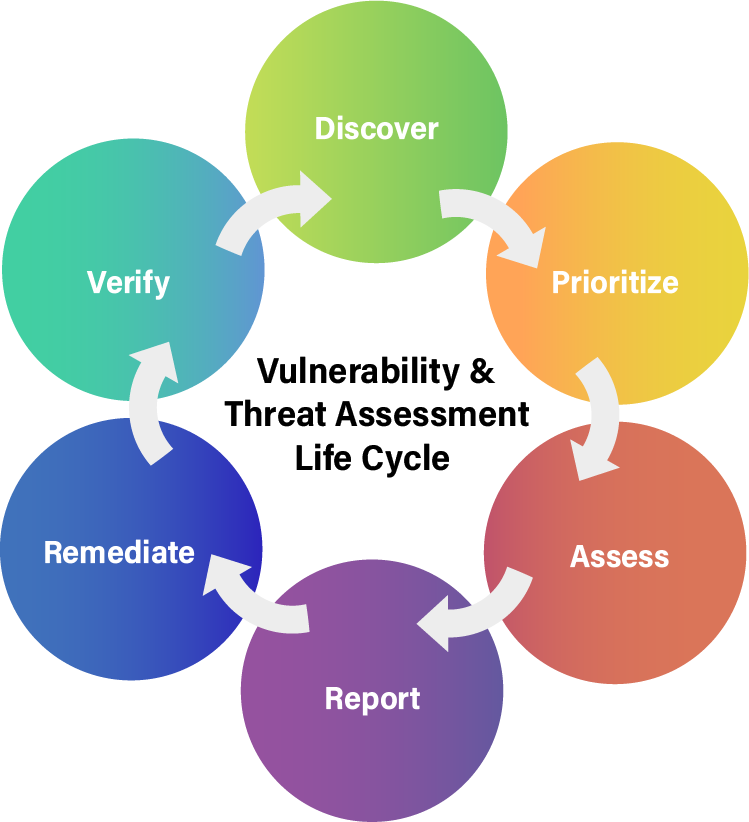 www.appa.org
www.appa.org
vulnerability threat cycle life higher why ed appa consultants pandemic deal care they do september october
Pin On Resilience - Adaptation - Hazards
 www.pinterest.com
www.pinterest.com
risk assessment hazards disasters response hazard vulnerability thegeographeronline health template geography volcanic factors safety responses natural resilience report human between
Hazard Vulnerability Assessment (HVA) | PDF
 id.scribd.com
id.scribd.com
What Is Vulnerability Management? - Astra Security Blog
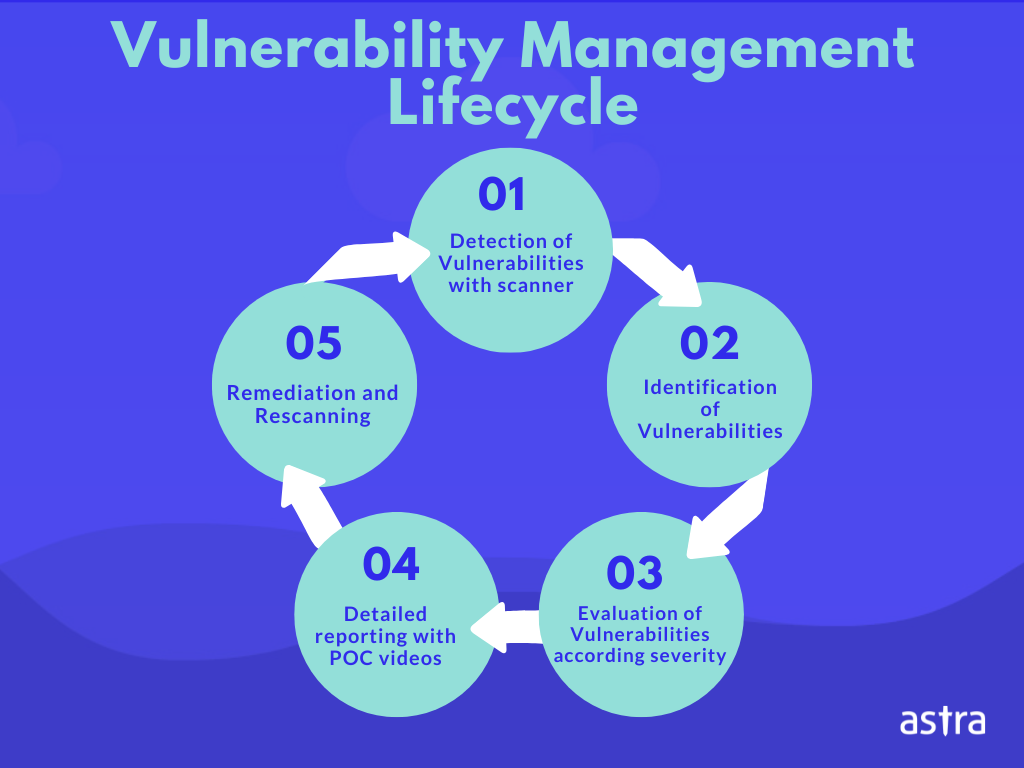 www.getastra.com
www.getastra.com
Archived - All Hazards Risk Assessment Methodology Guidelines 2011-2012
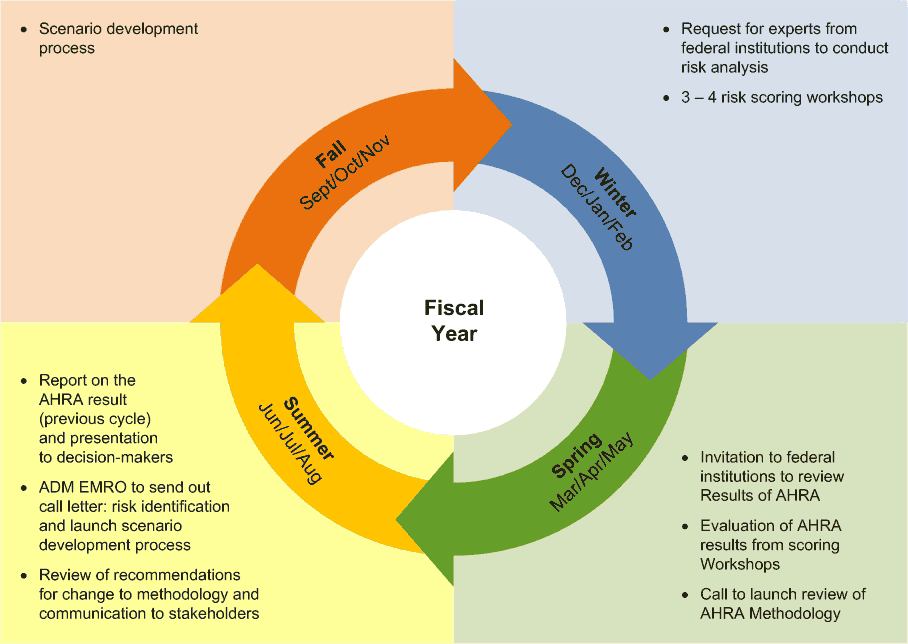 www.publicsafety.gc.ca
www.publicsafety.gc.ca
Hazard Vulnerability Assessment (HVA) Tool | ASHE
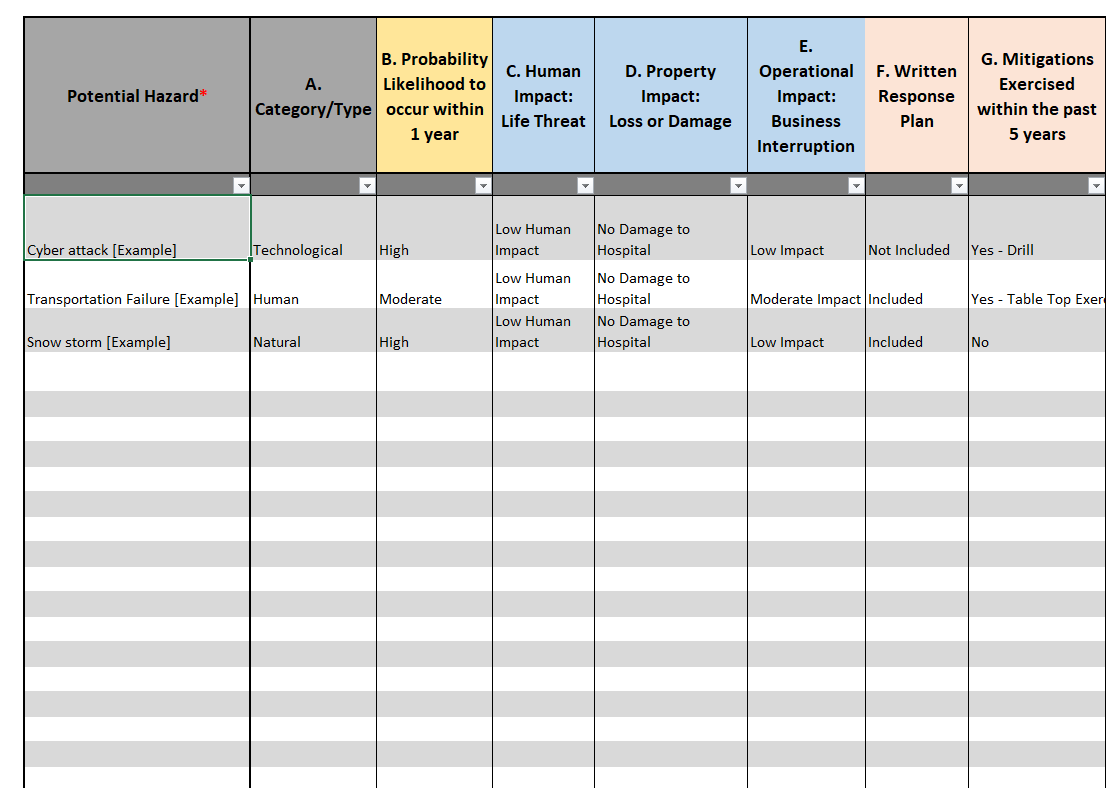 www.ashe.org
www.ashe.org
Hazard Vulnerability Analysis | HFM Wiki | Fandom
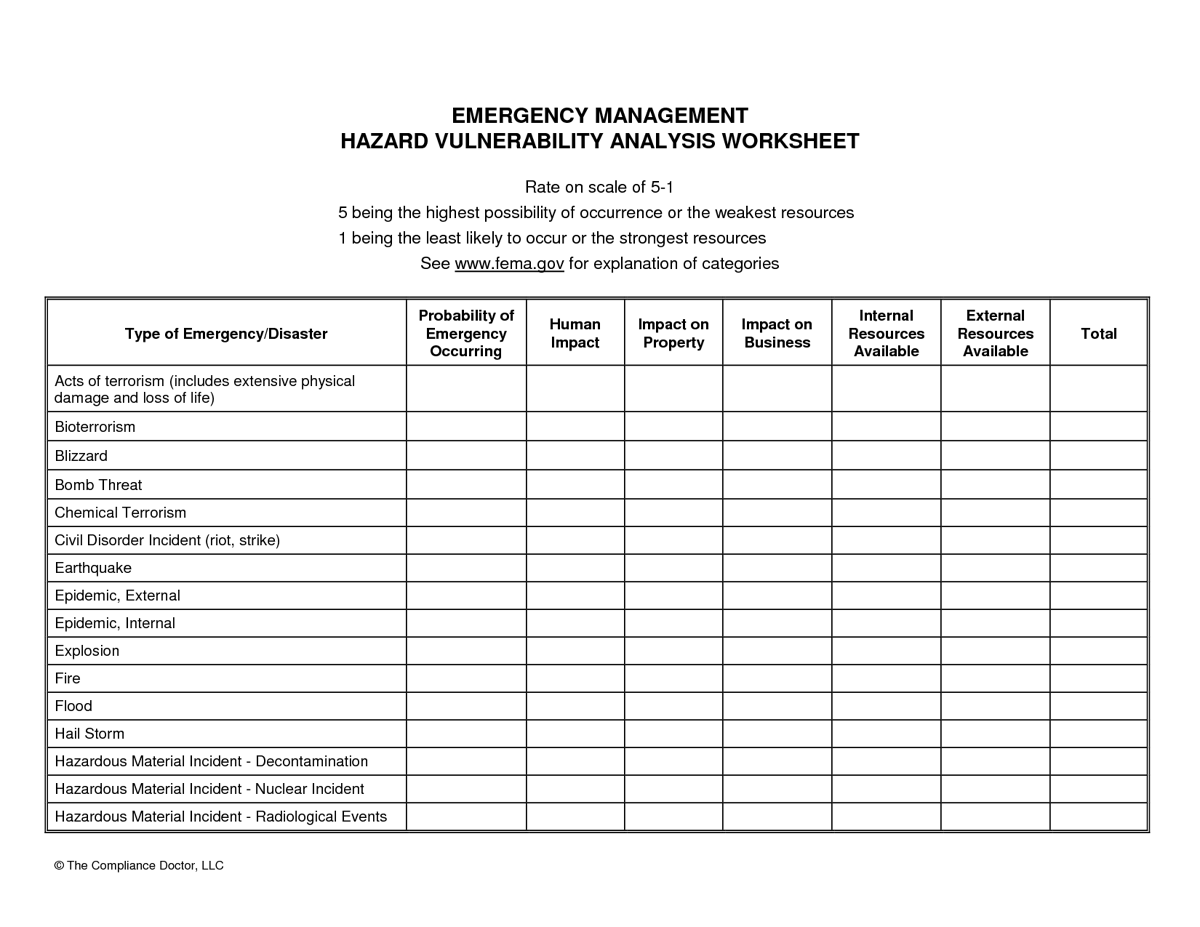 hfm.fandom.com
hfm.fandom.com
PPT - Hazard And Vulnerability Assessment PowerPoint Presentation - ID
 www.slideserve.com
www.slideserve.com
vulnerability hazard assessment ppt presentation powerpoint slideserve
Hazard, Vulnerability And Capacity Assessment For Community Based
 www.rcrc-resilience-southeastasia.org
www.rcrc-resilience-southeastasia.org
vulnerability assessment capacity hazard disaster community preparedness based resilience purpose
Sample Hazard Vulnerability Analysis | Analysis, Vulnerability
 www.pinterest.co.kr
www.pinterest.co.kr
vulnerability hazard
Solved Conduct A Hazard Vulnerability Analysis. Score It, | Chegg.com
 www.chegg.com
www.chegg.com
Risk Assessment And Vulnerability Analysis - Sigma Earth
 sigmaearth.com
sigmaearth.com
Vulnerability Assessment Tools & Checklists - ManageEngine
 www.manageengine.com
www.manageengine.com
vulnerability scanning remediation capabilities looming
Hazard Vulnerability Analysis Template
 syamil.itsnudimension.com
syamil.itsnudimension.com
hazard vulnerability pandemic gov insured continuity specific itsnudimension syamil
Vulnerability Assessment Scanning Tools List 2018 - ESecForte
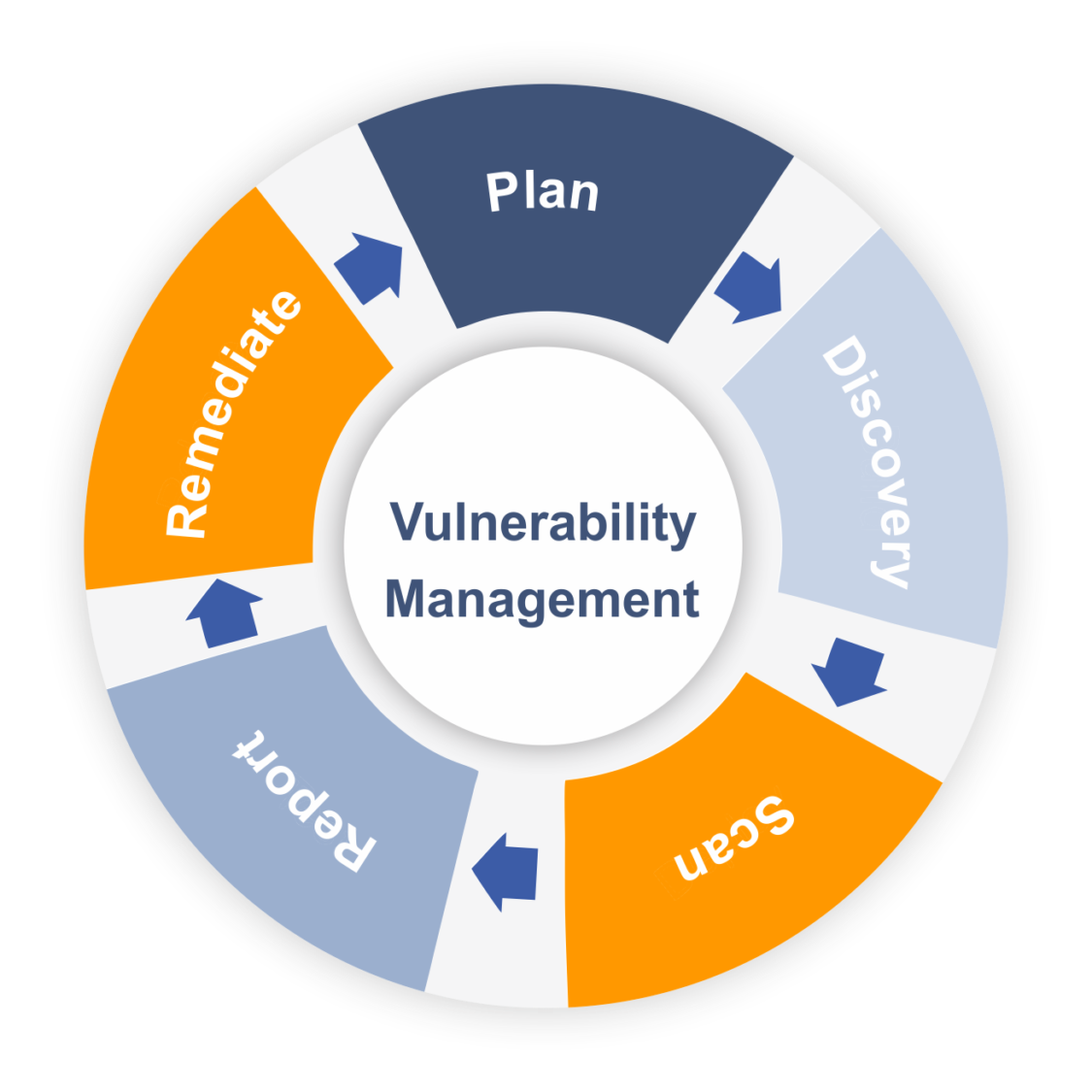 www.esecforte.com
www.esecforte.com
vulnerability scanning assess
Hazard Vulnerability Analysis - RBC Limited
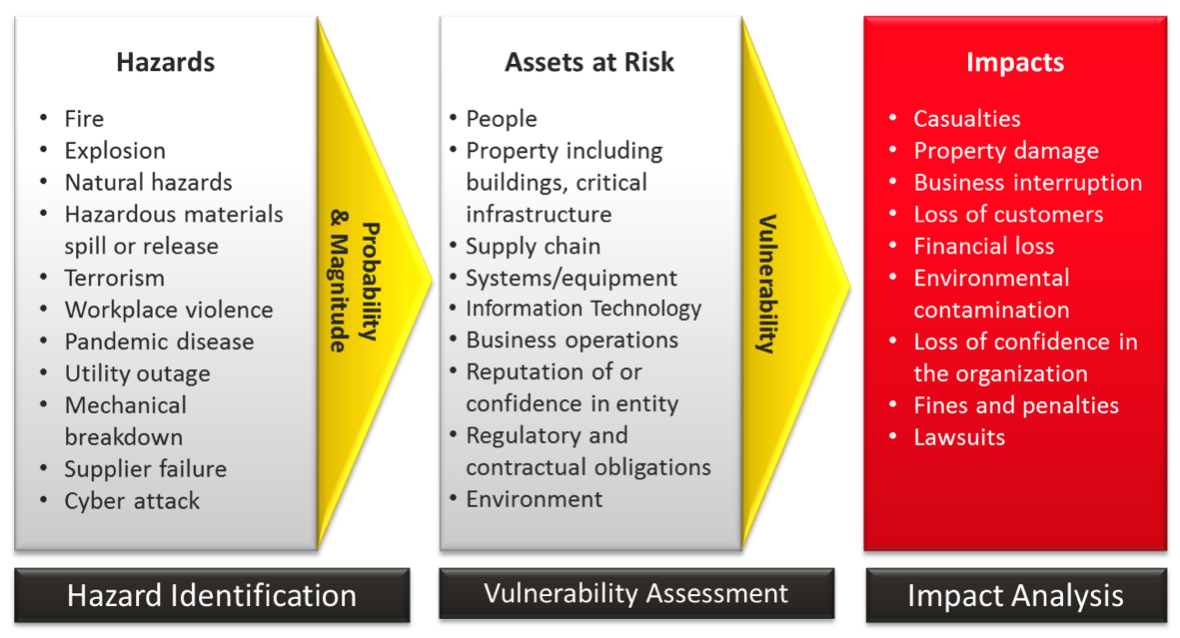 www.rbclimited.com
www.rbclimited.com
vulnerability hazard analysis assessment rbc chart plan emergency disaster
Flight Planning For Drone Flight|Hazard Vulnerability Assessments
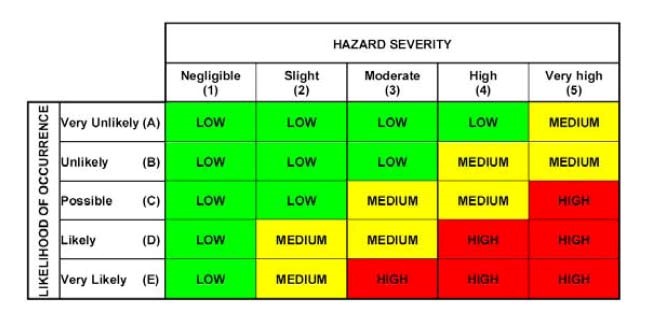 www.dronepilottrainingcenter.com
www.dronepilottrainingcenter.com
vulnerability hazard matrice probabilità rischi gravità graph hva
The Vulnerability Management Lifecycle (5 Steps) - CrowdStrike
 www.crowdstrike.com
www.crowdstrike.com
vulnerability lifecycle crowdstrike assess cybersecurity
HAZARD AND VULNERABILITY ASSESSMENT TOOL NATURALLY | Chegg.com
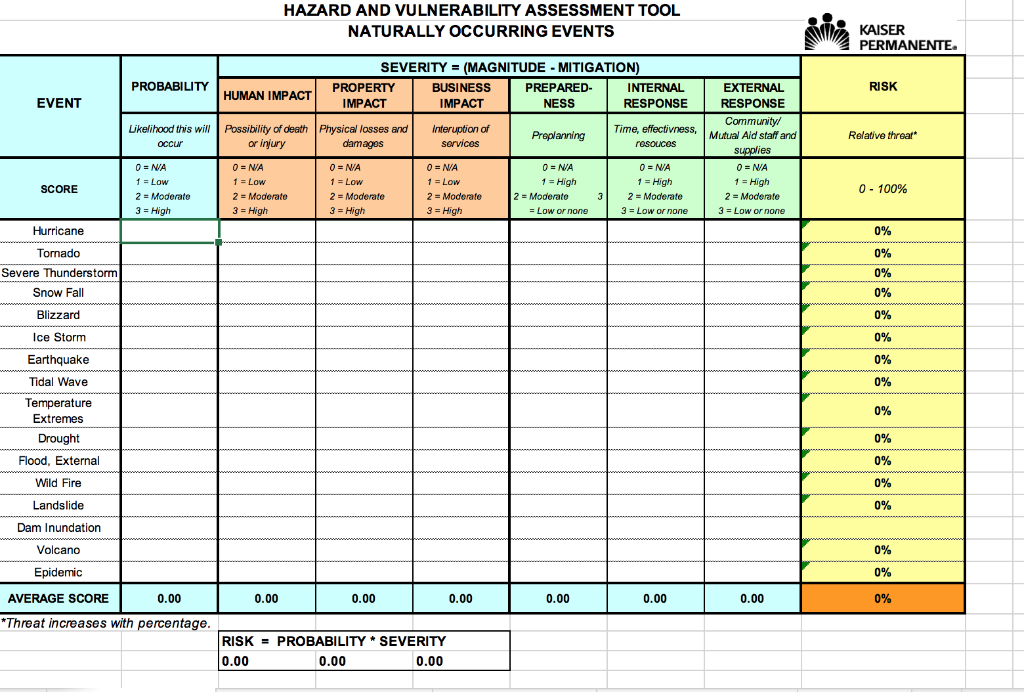 www.chegg.com
www.chegg.com
vulnerability hazard kaiser naturally occurring hasn solved
Editable Updated Guidelines For Fast Systems In Hazard Assessment
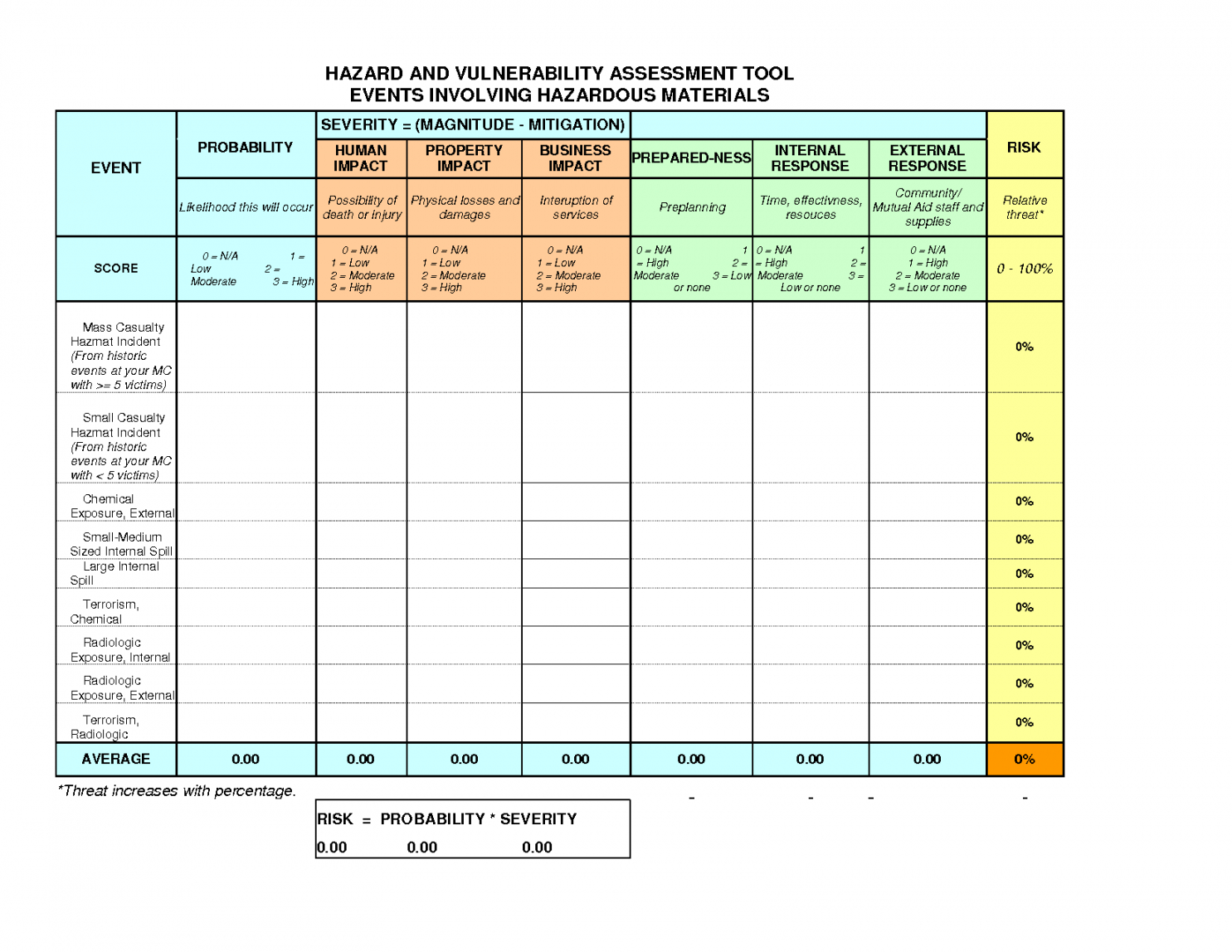 dremelmicro.com
dremelmicro.com
assessment vulnerability hazard template analysis fast pdf editable systems guidelines updated dremelmicro
Hazard Vulnerability Capacity Assesstment B
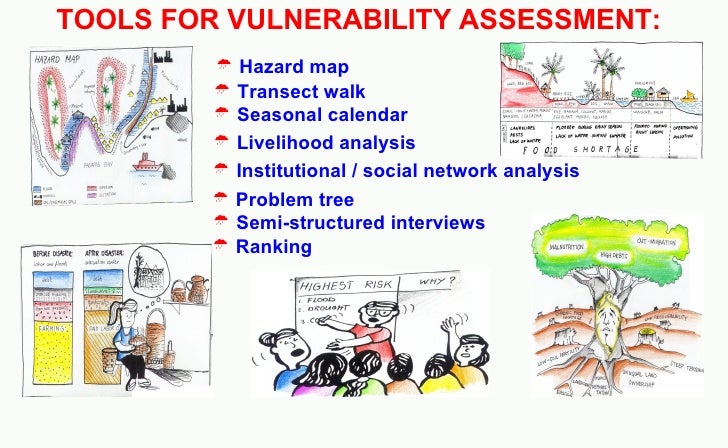 www.slideshare.net
www.slideshare.net
vulnerability hazard transect
5.5 Risk Assessment Methods
 www.cdema.org
www.cdema.org
vulnerability threat hazard mapping equation methodology
Hazard And Vulnerability Assessment Tool | PDF | Hazards | Emergency
 www.scribd.com
www.scribd.com
Hazard Vulnerability Assessments
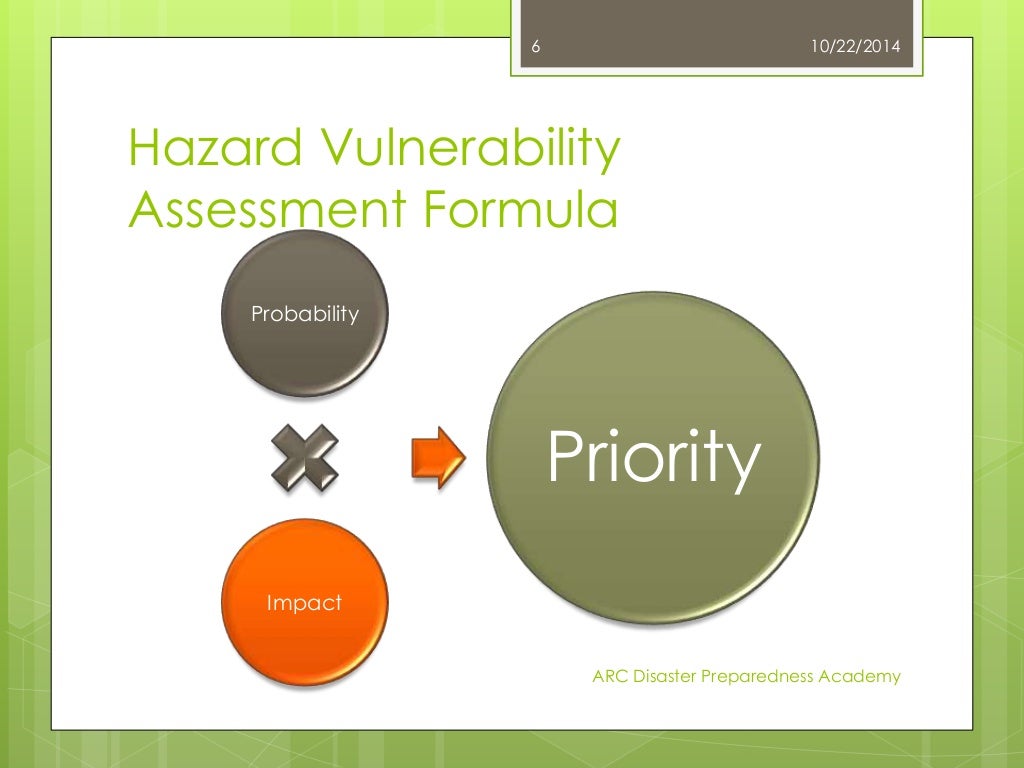 www.slideshare.net
www.slideshare.net
vulnerability hazard
Hazard Vulnerability Assessment | My XXX Hot Girl
 www.myxxgirl.com
www.myxxgirl.com
Customized Home Hazard Vulnerability Assessment — Doberman EMG
 www.dobermanemg.com
www.dobermanemg.com
The Five Stages Of Vulnerability Management
 blog.teamascend.com
blog.teamascend.com
vulnerability protecting analyzing aimed prioritizing multiple
How To Perform A Vulnerability Assessment: A Step-by-Step Guide
 www.intruder.io
www.intruder.io
vulnerability discovery
Risk Assessment Matrix With Vulnerability And Threat Level Formulating
 www.slideteam.net
www.slideteam.net
Vulnerability lifecycle crowdstrike assess cybersecurity. Solved conduct a hazard vulnerability analysis, using the. Vulnerability and threat assessments for higher ed: what are they and