← gravity falls bill cipher with standly Cipher pandas trust no one nature background hd wallpaper Trust wallpaper hd wallpapers pc background full 1080 1920 popular most →
If you are looking for How to hack a phone: 7 common attack methods explained | CSO Online you've visit to the right web. We have 35 Pictures about How to hack a phone: 7 common attack methods explained | CSO Online like What is hacking and how does hacking work?, Hacking: Learn How to Avoid Being Hacked - Phambano Technology and also You Have Been Hacked: 5 Killer Ways to Undo Hacking | IT Briefcase. Read more:
How To Hack A Phone: 7 Common Attack Methods Explained | CSO Online
 www.csoonline.com
www.csoonline.com
How Do Hackers Hack?
 www.securitymetrics.com
www.securitymetrics.com
hack hackers
How To HACK 455 MILLION Websites | WordPress Hacking - YouTube
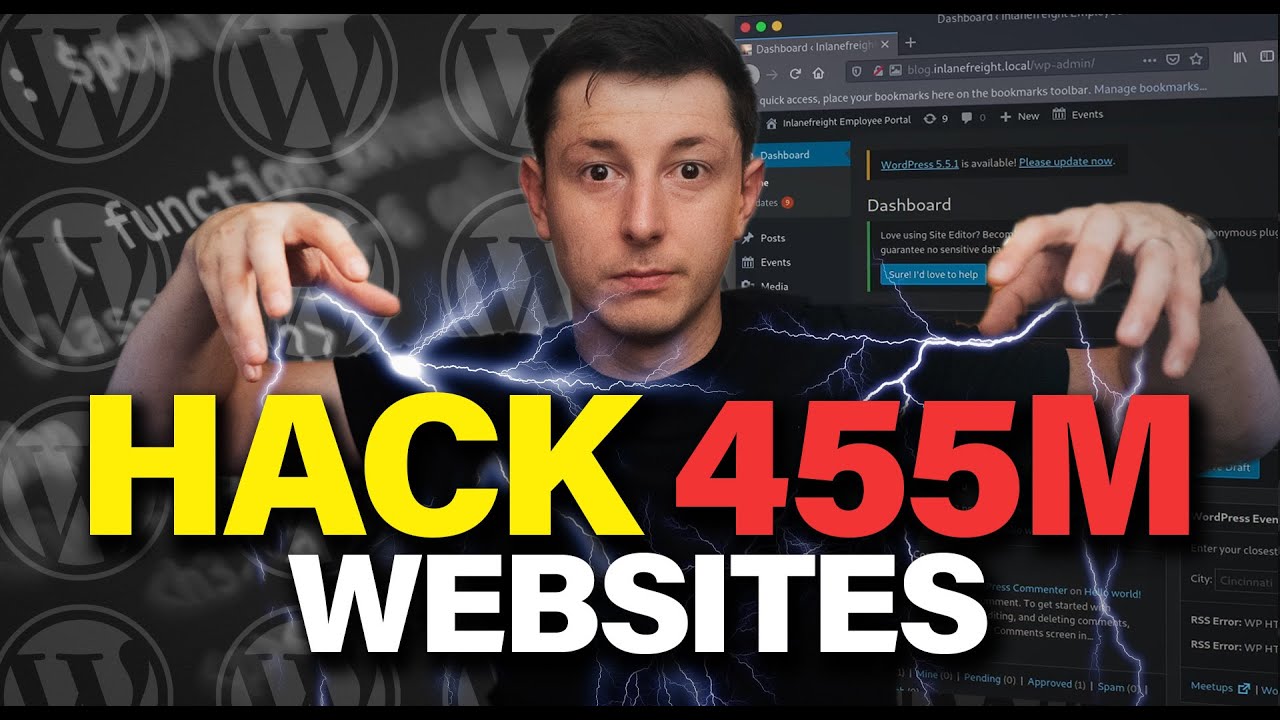 www.youtube.com
www.youtube.com
Ethical Hacking In 12 Hours - Full Course - Learn To Hack! - YouTube
 www.youtube.com
www.youtube.com
What Is Hacking And How Does Hacking Work?
 usa.kaspersky.com
usa.kaspersky.com
O Que é Hacking? | Definição De Hacking
 www.avast.com
www.avast.com
"How Hack" - YouTube
 www.youtube.com
www.youtube.com
Cyber Safety And Hacking Facts - Fascinating Cyber Facts
 factcyber.blogspot.com
factcyber.blogspot.com
Why Do Hackers Hack? [5 Big Reasons Explained]
![Why Do Hackers Hack? [5 Big Reasons Explained]](https://www.appknox.com/hubfs/xePRPu5w-2.webp) www.appknox.com
www.appknox.com
How Not To Get Hacked: Introduction - YouTube
 www.youtube.com
www.youtube.com
How To Hack A Heartbreak By Kristin Rockaway | Goodreads
 www.goodreads.com
www.goodreads.com
How Hackers Hack - New Horizons 123
 newhorizons123.com
newhorizons123.com
Instagram Hacked? How To Get Your Account Back - Norton
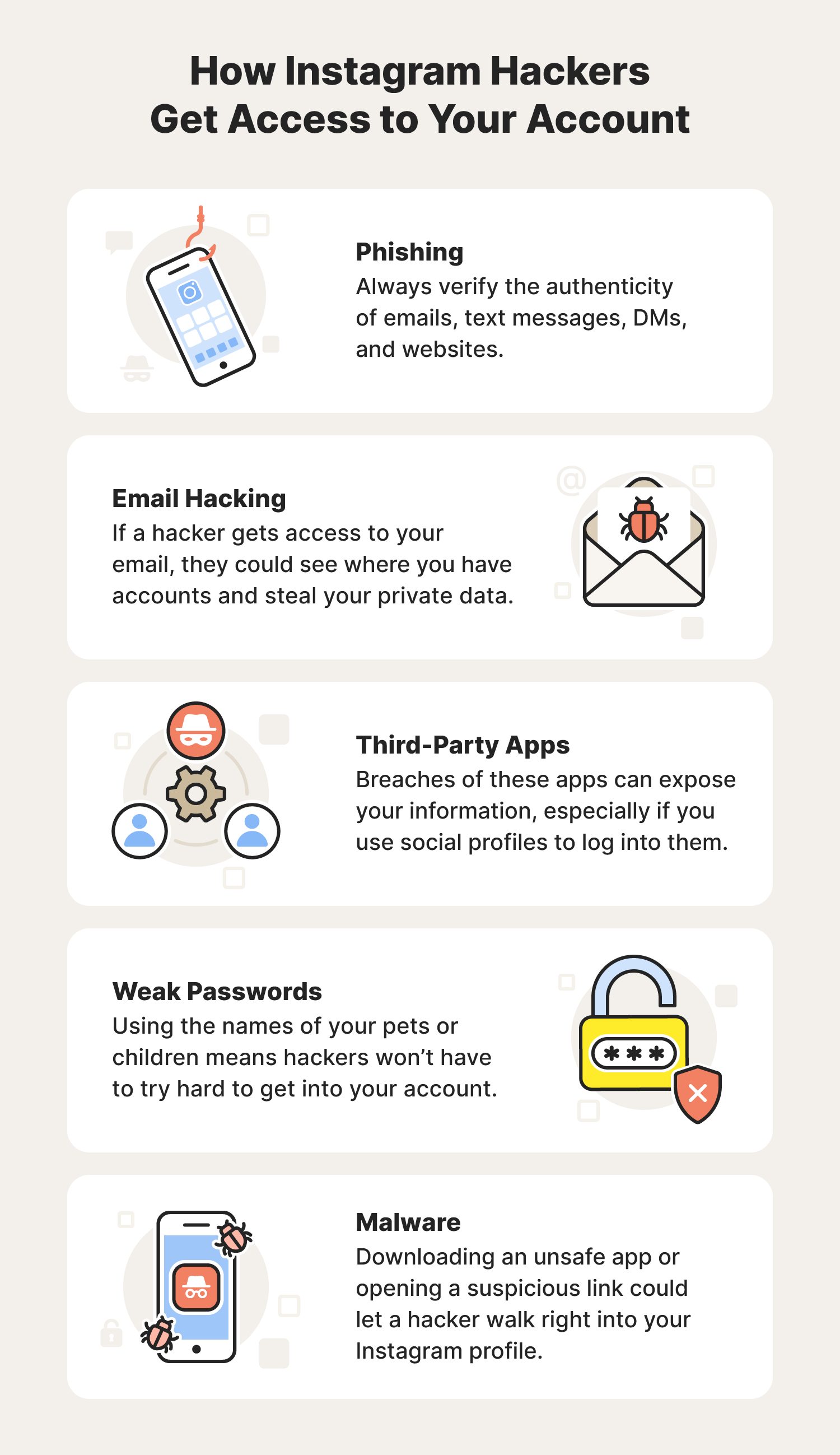 us.norton.com
us.norton.com
Until Media Cares About Its Security, Hackers Will Still Steal
 www.recode.net
www.recode.net
hacked hackers recode
The Ultimate Guide To Learn How To Hack
 digitalskills.miami.edu
digitalskills.miami.edu
The Weirdest Hacking Techniques You’ve Never Heard Of
 www.pandasecurity.com
www.pandasecurity.com
HackTheBox: Harnessing The Power Of Ethical Hacking For Skill
 blog.parrot-pentest.com
blog.parrot-pentest.com
Pin On Hmm
 www.pinterest.com
www.pinterest.com
hackers
Securing Wifi In Organization | Wifi Network Security & Wifi Security Types
 www.eccouncil.org
www.eccouncil.org
Why Do Hackers Hack? Perhaps Not For The Reasons You Think
 techhq.com
techhq.com
hack hackers why do hacker not internet haris database elias bounty just
The Different Types Of Hacking Techniques Explained: A Helpful Guide
 www.sdgyoungleaders.org
www.sdgyoungleaders.org
hacking techniques theft helpful use gain
Hot Null Byte How-Tos — Page 30 Of 39 « Null Byte :: WonderHowTo
 null-byte.wonderhowto.com
null-byte.wonderhowto.com
How To HACK Any Password?! - YouTube
 www.youtube.com
www.youtube.com
Use This Undawn Hack & Mod To Get Unlimited Points And Resources! IOS
 www.youtube.com
www.youtube.com
Comment Se Faire Passer Pour Un Hacker Cmd - Communauté MCMS™.
 mcmscommunity.org
mcmscommunity.org
THE COMPLETE GUIDE TO COMPUTER HACKING: All What You Needs To Learn To
 www.amazon.in
www.amazon.in
🔥 Download To Pretend Be A Hacker There S Nothing Like Hackertyper By
 wallpapersafari.com
wallpapersafari.com
hacker wallpaper pretend theres nothing like hacking desktop
Google Hacking: What Is A Google Hack?
 www.acunetix.com
www.acunetix.com
Differences Between Hacker And Lamer | BULB
 www.bulbapp.io
www.bulbapp.io
Hacking: Learn How To Avoid Being Hacked - Phambano Technology
 www.phambano.org.za
www.phambano.org.za
hacking hacked hacker pengenalan dll python za
Hacking: Hacking For Beginners Guide On How To Hack, Computer Hacking
 www.amazon.in
www.amazon.in
hacking hack basics ethical josh thompsons kindle
You Have Been Hacked: 5 Killer Ways To Undo Hacking | IT Briefcase
 www.itbriefcase.net
www.itbriefcase.net
hacking undo hacked been killer ways hernandez independent catherine author technology featured article
How To Learn Hacking: The (step-by-step) Beginner's Bible For 2024
 www.hackthebox.com
www.hackthebox.com
How To Protect Firewalls From Hacking ? | Managed Cyber Security
 firewall.directory
firewall.directory
Hacking Smartphones Running On MediaTek Processors
 thehackernews.com
thehackernews.com
hack hacking mobile mediatek smartphones android processors running discovered exploited dangerous remotely devices backdoor processor could been has
Cyber safety and hacking facts. You have been hacked: 5 killer ways to undo hacking. Hacking smartphones running on mediatek processors